Earlier this year, CENTR published an update of the security maturity model on its website. This security maturity model allows companies to check their maturity level in the field of information security. The idea behind the model is to give people in charge of information security in organisations some extra 'ammunition' when they go to their management to ask for more measures in the field of security.
Anyone can use the model freely, provided that feedback is given to the authors regarding changes to the model. To this end we requested a licence agreement.
Five steps in incident management
‘Our model uses the NIST structure (National Institute of Standards and Technology) cybersecurity framework, and is built around the five steps of the incident management process. The cybersecurity framework is a set of guidelines for companies to be better prepared for the detection of, and response to, cyber-attacks,’ explains Kristof Tuyteleers, cybersecurity officer at DNS Belgium.
- Establish: establish a framework to manage cybersecurity risks.
- Prevent: prevent cyber incidents from happening.
- Detect: detect incidents. ‘Without a doubt the most challenging step’, says Kristof. ‘Because many organisations don't even appear to know about any incidents because their detection system is not working properly.’
- Respond: how will you respond to security incidents.
- Recover, finally, is about restoring your normal activities after an incident. What did you learn from this and what will you be doing to avoid a repetition of the incident.
Six maturity levels
There are six maturity levels for each of these five steps in the security maturity model. ML0 (maturity level 0) stands for ‘non-existing’, when an organisation does nothing in the field of security. And then it goes from ‘incomplete’, ‘performed’, ‘managed’ and ‘measured’ to ‘improving’. At that highest level, processes are evaluated and adapted to changing needs.
An organisation receives a number of statements for each maturity level to which they need to answer yes or no. As soon as you answer a statement in a section with a no, you fall back a level.
‘Globally it seems we have advanced as a community compared to 2018'
Advancing as a community
The figures regarding the benchmark we carried out based on the maturity model are out now and the first cautious conclusions can be drawn. ‘The idea here is not to review individual results, let alone publish them. ‘But globally it seems we have advanced as a community compared to 2018’, determined Kristof.
‘In many countries, including Belgium, you have to be able to prove that you have an information security policy that meets a particular standard, usually the ISO/IEC 27001 standard’, says Kristof. ‘That is also the reason why established advanced so much: managing security is a first step, but it is a step many organisations have now – forcibly or not – taken.’
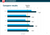
Since 2018, the maturity level has been broken down into the five steps of the model. The light-blue bar shows the progress.
ISO standard
The model provides a very good idea of the extent to which a company complies with the NIS-legislation (Network and Information Security) because it maps the content of the ISO- standard on the structure of the NIST cybersecurity framework. Every ISO/IEC 27001-certified registry should at least achieve level 3 (baseline on the picture), Kristof believes.
The information security ISO standard contains requirements to show that the organisation is continuously improving its security policy. Our model can help to identify areas for improvement and to draw up a planning. For example, you could deal with the sub-aspects with the lowest maturity level, or a domain where you score below expectations.
This is also how DNS Belgium uses the model. We set ourselves the obligation to make at least twelve improvements every year", says Kristof. ‘That is getting harder every year, because in the beginning you make big steps, but gradually the areas for improvement become smaller. Of course the security landscape is constantly changing and new risks keep on appearing. This is why improvement is always possible. And the model helps to draw up a goal-oriented planning.'

With this article, we support the United Nations Sustainable Development Goals.
